HTTP parameter pollution is a web application vulnerability in which it pollutes the HTTP parameters to achieve the specific task which are different from the intended behaviour of the web application. In HTTP Parameter pollution, attacker will append an extra parameter to an HTTP request to perform an unintended behaviour.
When you pollute any HTTP parameter, we can only view the results as the code is being executed on the server side which is invisible to us. This vulnerability can be found on both client side and server-side.
Server-side HTTP Parameter Pollution
In this type of vulnerability server will perform the checks on parameters we are sending. For example:
https://example.com/transfer?from=1007&to=2654&amount=1000
Here we are passing three parameters such as from, to and amount to initiate a transfer from one account to another account. However, the web server is improperly configured, and the developers of this application only expect one from parameter. Here a malicious attacker can add an additional from parameter to fool the web application server and they can make the transaction from the account which they don’t own.
https://example.com/transfer?from=1007&to=2564&amount=1000&from=2202
Client-side HTTP Parameter Pollution
In client-side HTTP parameter pollution, the vulnerability arises when a web application embeds user inputs in URL in unsafe manner .it will also allow an attacker to modify and inject parameters into a URL to create an effect on the client side. An attackers can exploit this issue by construct a URL, if that URL is visited by another user application and modifies URLs inside the response by adding extra query string arguments and occasionally altering existing ones Below, we can see an example to describe how much effective this vulnerability will cause.
http://example.com/invite.php?attendee=1337%26action=new_invite%26attendee=3301
This is a URL to send a private invite form to an unexpected recipient.
Here an attacker would append %26 which is encoding of & sign after the HTTP parameter attendee to fool the server-side code to think it all belongs to one parameter. if the backend code only read a value from the first attendee, then will not read the next two parameters if we used the & sign. when the URL is parsed as %26 as interpreted, as & and the URL would be look like:
http://example/invite.php?attendee=1337&action=new_invite&attendee=3301
and if this is included in an href tag
<a href=”http://example.com/invite.php?attendee=1337&action=new_invite&attendee=3301">Confirm RSVP </a>
Then an unsuspecting user would click this and send an invite to someone
Example
We will now look for an example. You are trying to login to your social media account, and you enter your password and your realised that you forgot your password. Now the only way is reset your password.
An HTTP Request for resset password will be like this POST /resetPassword HTTP/1.1 Host: example.com Content-Type: application/xml Content-Length: 36
emailAddress=User@example.com
Here you will receive a password reset link after you enter your email address. An attacker can go and try to pollute the HTTP parameter in the request to receive the victim password reset link.
An Example of attackers HTTP Request could be like this POST /resetPassword HTTP/1.1 Host: example.com Content-Type: application/xml Content-Length: 70
emailAddress=regularUser@example.com&emailAddress=attacker@example.com
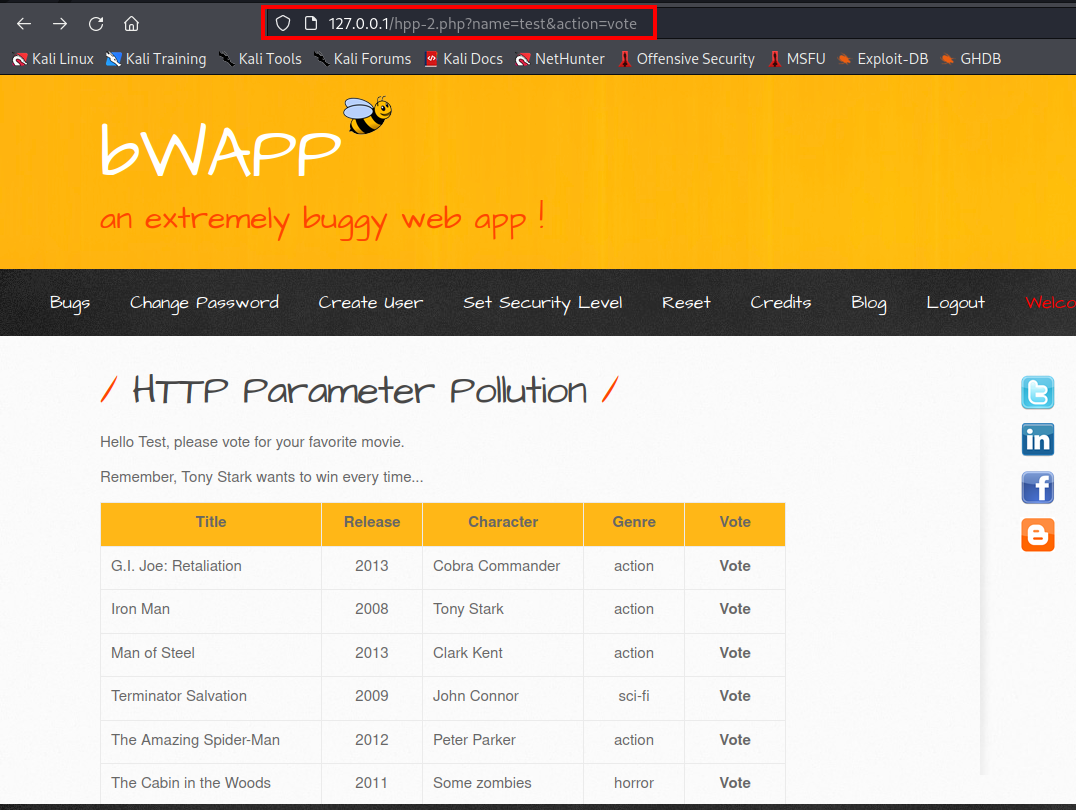
Here we will look for a real-world scenario and you can download this vulnerable web application using http://www.itsecgames.com/download.htm
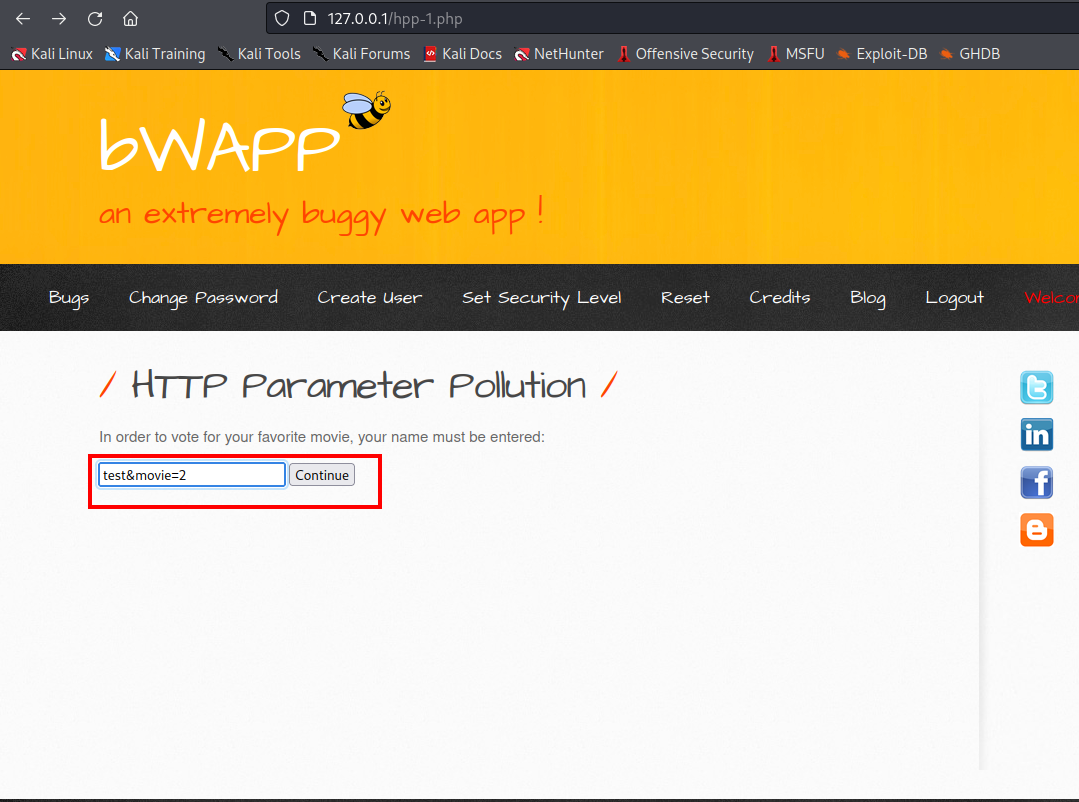
- To vote for your favourite movie first you need to enter your name.
- we can see current parameter such as name and action
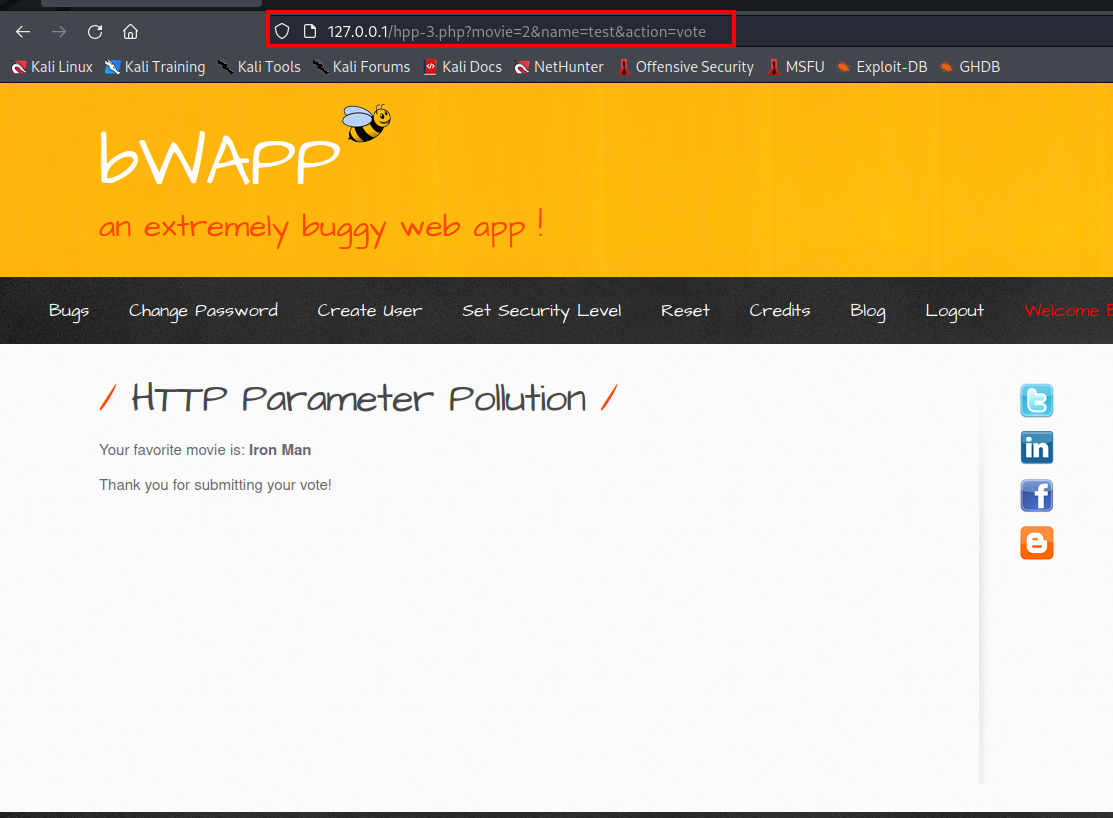
- After voting your favourite movie, the parameter is movie, name, and action.
- Now we can check if it is vulnerable to HTTP parameter or not by adding another parameter movie.
- It is saying that your favourite movie is spiderman. It means they accepted second parameter not the first one.
- So now what we want is when any other users click any movie the vote must go to iron man by adding parameter.
- If you click any other movie as your favourite the vote will only goes to the second movie because of HTTP parameter pollution vulnerability.
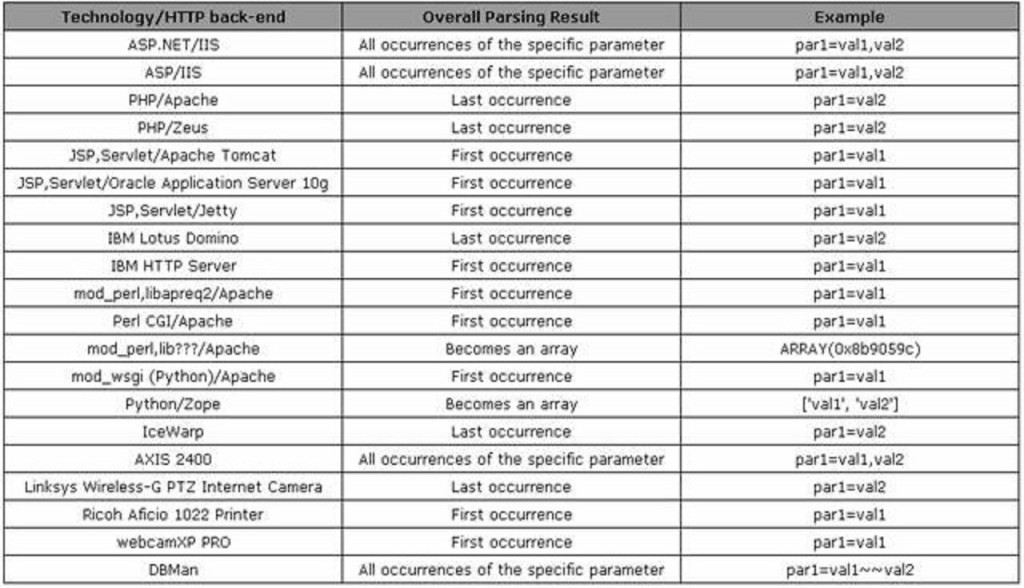
- From below table you can check the different behaviour of interpreting parameters on different web servers and technologies: -



IMPACT
- It helps to bypass input validation checks.
- Override existing hardcoded HTTP Parameters.
- Helps to bypass Web Application Firewall (WAF) rules.
- It provides routes for attacks like SQL injection and cross site scripting (XSS).
How to Prevent
- A proper input validation needs to be performed.
- All user supplied input which are reflecting on the HTML source code of the HTTP response should be encoded.