What is SSH Tunnelling? Where and How to use it?
SSH tunnelling is a method of transporting “data of our choice” over an encrypted SSH connection. It can be used to implement VPNs (Virtual Private Networks) and access intranet services across firewalls.
SSH is a standard for secure remote logins and file transfers over untrusted networks. It also provides a way to secure the data traffic of any given application using port forwarding, basically tunnelling any TCP/IP port over SSH. This means that the application data traffic is directed to flow inside an encrypted SSH connection so that it cannot be eavesdropped or intercepted while it is in transit. SSH tunnelling enables adding network security to legacy applications that do not natively support encryption.
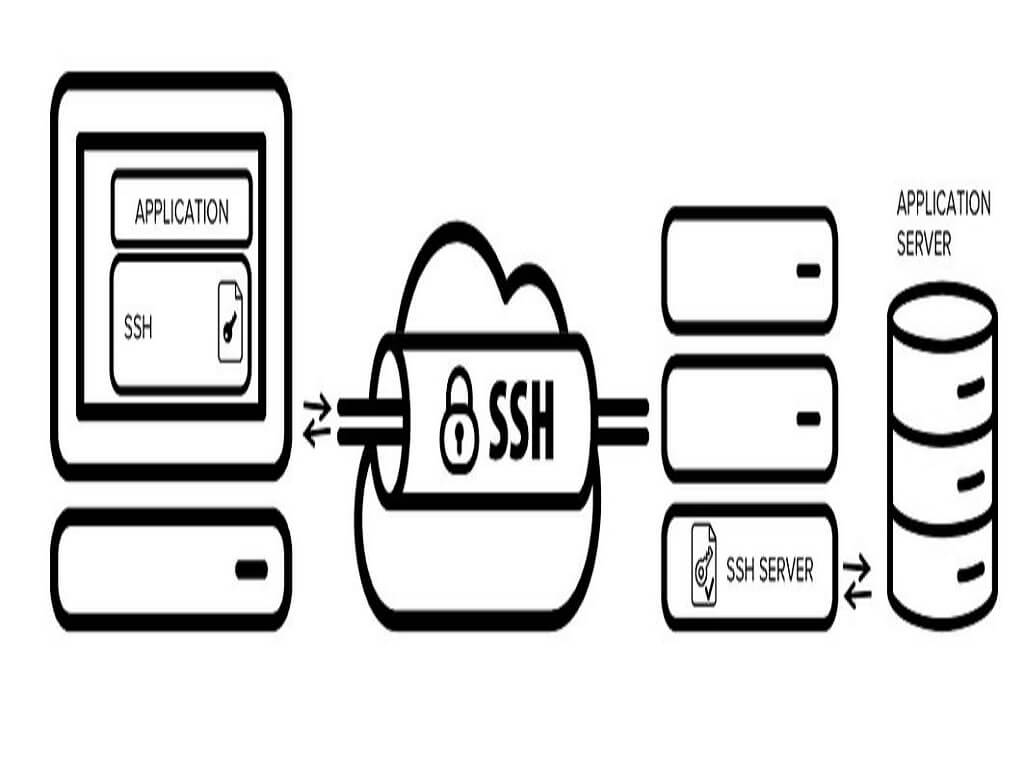
SSH Tunnelling
In the figure above, a secure connection will be formed between SSH Client and SSH Server through SSH Tunnelling.
Here in the Fig 1, The Application uses SSH to connect to the Application server. When the SSH tunnelling is enabled, the application contacts to a port on the local machine or host where the SSH client is listening. Next, the SSH client forwards the application over its encrypted tunnel to the server. The server then connects to the actual application server - usually on the same machine or in the same data centre as the SSH server. The communications within the application is thus secured.
SSH Tunnelling can be used in number of ways such as to add encryption to legacy applications, going through firewalls, and IT professionals use it for opening backdoors into the internal network from their host machines. It can also be abused by hackers and malware to open access from the Internet to the internal network
Use cases of SSH Tunnelling (also called as SSH Port Forwarding)
- Local Port Forwarding
- Remote Forwarding
- Opening Backdoors
Local Port Forwarding
Local forwarding is used to forward a port from the client machine to the server machine. Basically, the SSH client listens for connections on a configured port, and when it receives a connection, a tunnel is opened between the SSH Client and the SSH server.
This technique allows the users to access local network resources that are not exposed to the Internet. Suppose you want to access a database server at your office from your home without compromising the security of your office network. This can be done if you have access to an SSH server at the office, and that SSH server allows connections from outside the office network, then you can connect to that SSH server from home and access the database server as if you were in the office.
The above-mentioned scenario can be achieved by establishing an SSH connection with the SSH server and request the SSH client to forward traffic from a specific port from your local PC—for example
OpenSSH uses -L for local port forwarding
ssh -L local_port:remote_address:remote_port username@server.com
Here the local_port is the port on your local PC that will be used by the SSH Tunnel remote_address and remote_port are the IP address and port number of the database server on the office network.
ssh -L 8888:192.168.9.100:4444 shrishail.arridae.com
8888 is the local port on your PC. 192.168.0.100 and 4444 are the IP address and port number respectively of the database server shrishail.arridae.com
By default, anyone (even on different machines) can connect to the specified port on the SSH client machine. However, this can be restricted to programs on the same host by supplying a bind address:
ssh -L 127.0.0.1:8888:192.168.0.100:4444 shrishail.arridae.com
So only the programs on the local host (127.0.0.1) can be able to access the server.
Remote Port Forwarding
It is used when the Firewall is blocking the incoming connections from outside the network to your PC’s applications such as a web application running on port 8080. The web application is hosted in such a way that it cannot be accessed from outside the network but with the help of SSH Tunnelling, it can be accessed by attackers from outside the network.
In OpenSSH the option -R is used for Remote Port Forwarding
ssh -R 8080:localhost:80 pankaj.arridae.com
The above command allows anyone on the remote server (controlled by the attacker) to connect to TCP port 8080 on the remote server. The connection will then be tunnelled back to the client host, and the client then makes a TCP connection to port 80 on localhost.
Here the port 8080 is the remote port on the remote server. The localhost and 80 are controlled by the attacker. This means the attacker can listen on any port instead of just using 80. The attacker can also choose the host of their liking instead of just using local host to receive connections.
By default, OpenSSH only allows connecting to remote forwarded ports from the server host. However, the GatewayPorts option in the server configuration file sshd_config can be used to control this.
The following alternatives are possible:
GatewayPorts no #prevents connecting to forwarded ports from outside the server computer.
GatewayPorts yes # allows anyone to connect to the forwarded ports. If the server is on the public Internet, anyone on the Internet can connect to the port.
Opening Backdoors
Remote SSH port forwarding is commonly used by employees to open backdoors into the enterprise with and without knowing the consequences of their actions. For example, the employee may use AWS free tier server and log in from the office to that server, specifying remote forwarding from a port on the AWS server to some server or application on the internal enterprise network. Multiple remote forwards may be specified to open access to more than one application.
The employee would also set GatewayPorts yes on the server (most employees do not have fixed IP addresses at home, so they cannot restrict the IP address).
For example, the following command opens access to an internal SSH port at port 2222.
ssh -R 2222:blog.arridae.com:22
Installing ssh tunnel tool in Linux
This tool can easily be used to access remote ssh servers where the port forwarding is enabled using ssh tunnelling.
Before running the following command, make sure that pip is installed on your local machine.
pip install sshtunnel or git clone https://github.com/pahaz/sshtunnel.git cd sshtunnel/ python setup.py install
Usage:
sshtunnel --help
usage: sshtunnel [-h] [-U SSH_USERNAME] [-p SSH_PORT] [-P SSH_PASSWORD] -R
IP:PORT [IP:PORT ...] [-L [IP:PORT [IP:PORT ...]]]
[-k SSH_HOST_KEY] [-K KEY_FILE] [-S KEY_PASSWORD] [-t] [-v]
[-V] [-x IP:PORT] [-c SSH_CONFIG_FILE] [-z] [-n] [-d [FOLDER [FOLDER ...]]]
ssh_address